Your Guide to Identity Theft Protection Services

Think of an identity theft protection service as a personal, around-the-clock security team for your sensitive data. It’s a multi-layered defense system that does much more than basic security hygiene like using strong passwords. It acts as a comprehensive watchdog for your entire financial and digital life.
What Exactly Are Identity Theft Protection Services?
Imagine trying to personally guard every single door and window of a massive skyscraper all at once. You can’t. It’s impossible. Well, your personal information—your Social Security number, bank accounts, driver's license, and credit card numbers—is scattered across hundreds of digital locations just like that. This is precisely where identity theft protection services come into play.
Their real job isn't to make you invincible. They can't prevent a company you do business with from suffering a data breach. Instead, they provide a powerful early-warning system. They can spot your stolen information on the dark web almost as soon as it appears, giving you a heads-up before a criminal has the chance to use it to open a new credit card in your name.
To really get what these services do, it helps to break them down into their three core functions. Each one builds on the last to create a safety net for your identity.
The Three Pillars of Identity Protection
Most quality identity protection services are built on three fundamental pillars. Understanding how they work together is key to seeing their true value.
These three pillars—monitoring, alerting, and recovery—form the foundation of modern identity protection.
This visual helps illustrate how these services create a hierarchy of protection for you.
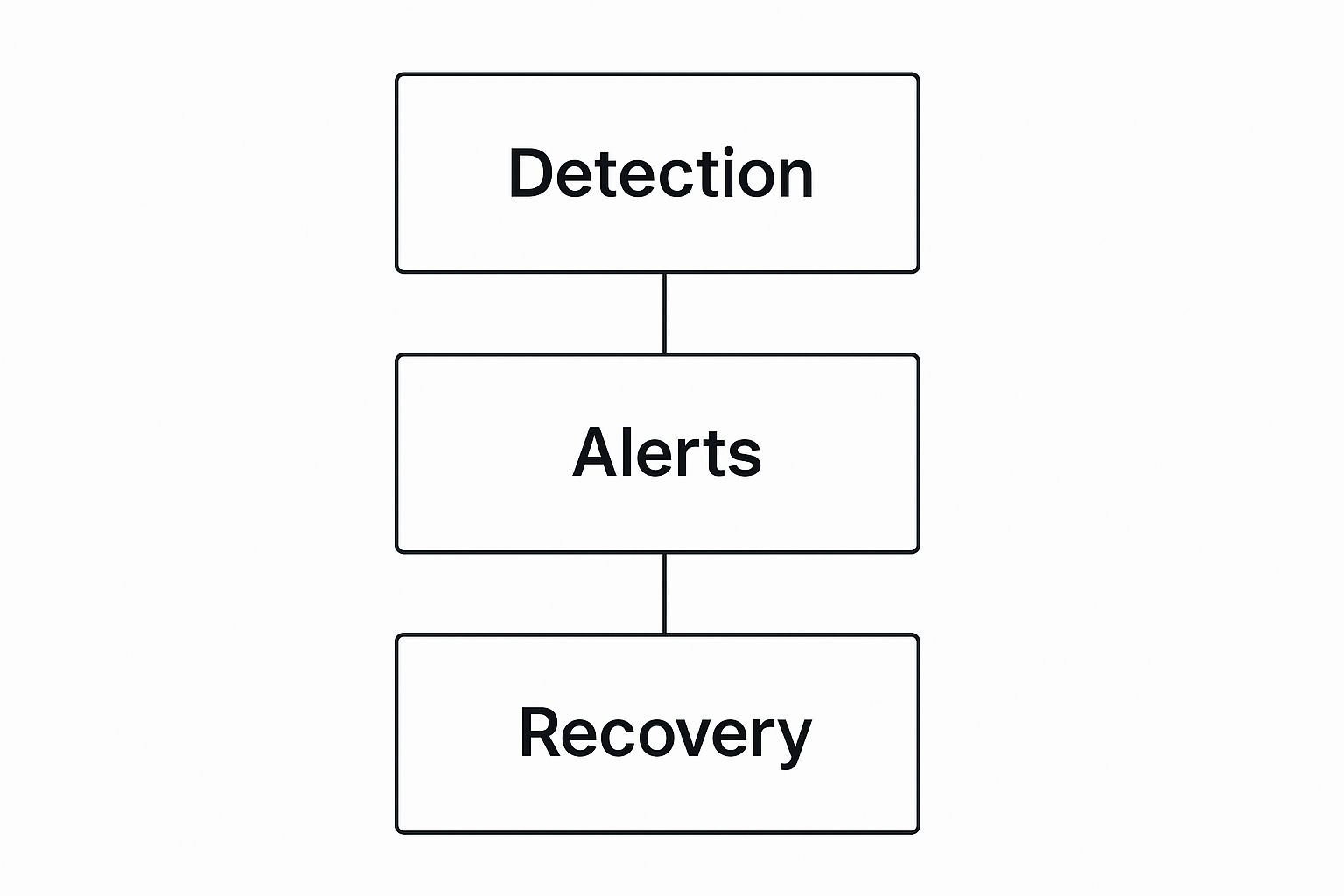
As you can see, everything starts with detection. That leads to a quick alert, which is all backed up by a solid recovery plan if things go wrong.
Why Proactive Defense Matters
This need for a proactive shield has fueled a booming market. As we move more of our lives online, from banking to healthcare, the opportunities for criminals to strike have multiplied.
This growth isn't just a business trend; it highlights a critical shift in consumer awareness. People are realizing that trying to monitor everything on their own is no longer realistic. If you're interested in the market forces behind this growth, you can get a deeper look by exploring the full analysis from Research Nester.
With the sheer number of data breaches today, it's safe to assume your information is already out there somewhere. The question is no longer if it will be compromised, but when a criminal will try to use it. Without a monitoring service, you might not find out about the fraud for months—usually when you get denied for a loan or a debt collector calls about an account you never opened.
And that brings us to the most important benefit these services offer.
The True Value Is Time and Peace of Mind
At the end of the day, you aren't just paying for software or alerts. You're buying back your time and investing in your peace of mind.
Trying to recover from identity theft on your own is a grueling, stressful, and time-sucking nightmare. Victims often report spending hundreds of hours on the phone with banks, credit bureaus, and government agencies, drowning in paperwork to clear their name. A protection service gives you a team of specialists to navigate that mess for you, turning a potential disaster into a manageable problem.
How These Services Actively Defend Your Identity

To really get how these identity theft protection services build such a strong defense, it helps to peek behind the curtain and see what’s actually going on. These platforms aren't just sitting back and waiting for something bad to happen; they're tireless digital watchdogs, actively guarding your information on multiple fronts at once.
Think of it like a high-tech security system for your house. You wouldn't just rely on a single lock on the front door. You’d have motion detectors, cameras, and window sensors all working together. That’s exactly what these services do for your personal data, using a whole suite of powerful tools to monitor the vast, messy digital world where your information lives.
The proof is in the numbers. The market for these services is on track to nearly double to $26.1 billion in the next few years. Why? Because they’re effective at fighting common threats like bank and utility fraud, and more people are turning to them as their first line of defense. You can see the full market analysis over at IMARC Group's website.
So, what's the secret sauce? Let's break down the core mechanics.
Scanning the Digital Underworld
One of the most important things these services do is dark web monitoring. The dark web is a hidden corner of the internet where criminals buy and sell stolen data from company breaches. It’s not a place you can just pop into on Google to see if your Social Security number is for sale.
Identity protection services use advanced web crawlers—think of them as specialized search bots—that can get into these shadowy marketplaces. They are programmed to constantly hunt for specific bits of your information, like:
When one of these crawlers spots a match—your data showing up on a hacker forum or an illegal online shop—it immediately triggers an alert for you. It’s the digital version of finding your stolen wallet for sale in a pawn shop. It’s a red flag telling you to act, and fast.
Keeping a Watchful Eye on Your Credit
The next layer of defense is credit monitoring. Your credit reports, which are held by the three major bureaus (Equifax, Experian, and TransUnion), are like a financial diary of your life. Naturally, they are a prime target for identity thieves.
These services watch your credit files for any changes, often spotting them within minutes. If you want to dive deeper into the basics, our guide on what is credit monitoring is a great place to start. When the service sees something suspicious, you get an alert.
Common activity that triggers a credit monitoring alert includes:
Getting that instant notification gives you a crucial head start to shut down fraudulent activity before it spins out of control.
Putting It All Together in a Real-World Scenario
Let's walk through a quick example to see how this all clicks into place.
Imagine your favorite online clothing store sends out an email: they’ve had a massive data breach. Hackers stole the whole customer database, including names, email addresses, and passwords.
Without an identity theft protection service: You might not even see that email for a few days. By then, a criminal could have already tested your leaked password on your bank account or email, locked you out, and started causing damage.
With an identity theft protection service:
This proactive shield turns what could be a full-blown crisis into a minor, manageable task. It catches the threat right at the beginning, buying you the precious time you need to lock down your digital life before any real harm is done.
Must-Have Features in a Protection Plan
Picking an identity theft protection service can feel a lot like trying to choose the right insurance policy. The options seem endless, the jargon is confusing, and you're left wondering what you actually need. Let's cut through the noise.
Think of it like buying a car. Brakes and airbags are non-negotiable safety features. A sunroof and a premium sound system? Nice, but not essential. This section is your guide to figuring out the "brakes and airbags" of identity theft protection, so you can get solid security without paying for bells and whistles you don't need.
The Foundation: Three-Bureau Credit Monitoring
First things first: any service worth its salt absolutely must include three-bureau credit monitoring. Your credit story is told across three different major bureaus—Experian, Equifax, and TransUnion. The catch is, they don't always share information instantly. A thief could open a new credit card in your name, and it might only show up on one of those reports at first.
If your service only watches one or two bureaus, you have a massive blind spot. It’s like having a security camera on your front door but leaving the back door and all the windows wide open. A criminal will always find the easiest way in. Monitoring all three isn't a luxury; it's the bedrock of real protection.
If finding an affordable way to get this complete view is your priority, you can check out our guide on the cheapest credit monitoring service to compare your options.
Your Digital Bodyguard: Comprehensive Dark Web Scanning
The next non-negotiable is dark web scanning. As we've discussed, the dark web is the shadowy marketplace where criminals buy and sell the personal information they’ve scooped up from data breaches. You need a service that’s constantly patrolling these hidden corners of the internet for you.
Think of it as having your own undercover agent. This digital operative knows where the illegal markets are and is always on the lookout for your specific credentials, including your:
When the service finds your data for sale, it sends you an immediate alert. This gives you a critical head start to change your passwords, freeze your credit, or take other protective steps before a criminal can use that information to become you.
The Lifeline: Full-Service Identity Restoration
This feature is your "in case of emergency, break glass" safety net. While monitoring and alerts are meant to stop a disaster before it starts, no service can promise 100% prevention. If a thief does manage to successfully steal and use your identity, you absolutely need full-service identity restoration.
This is arguably the single most valuable piece of any protection plan. It means you get a dedicated, U.S.-based case manager who does all the heavy lifting to clean up the mess. Honestly, the process of recovering a stolen identity is a nightmare. It can involve hundreds of hours of phone calls, mountains of paperwork, and endless follow-ups.
A restoration specialist takes that burden off your shoulders. They navigate the bureaucratic maze of credit bureaus, banks, and government agencies to clear your name and restore your good standing. Just to give you an idea of the scale, the IRS alone reported an average case processing time of 556 days for identity theft victims in fiscal year 2023. Having an expert handle that for you is priceless.
The global market for these services, valued at around USD 11.1 billion, is heavily concentrated in North America, where credit card fraud is a constant threat. This huge demand shows just how critical this kind of robust protection has become. For those interested in the market dynamics, you can find more in this comprehensive market report.
Comparing Essential vs. Optional Protection Features
To help you decide what's truly necessary for your situation versus what's just a "nice-to-have," this table breaks down common features by their priority level. Use it to gauge which plan offers the right balance of protection and price for your needs.
Ultimately, your goal should be to cover all the "Essential" bases first. From there, you can decide if the other features offer enough value to justify any extra cost.
Valuable Add-Ons to Consider
Once you've confirmed a plan has the essential trio locked down, you can start looking at extras that might be a good fit for your life.
The True Value of Proactive Monitoring

When you think about identity theft protection, it’s easy to focus on security software or slick dashboards. But the real value isn’t just about technology. It’s about reclaiming two of your most precious assets: your time and your peace of mind.
The difference between a proactive and a reactive approach to identity theft is night and day. It’s the gap between a minor inconvenience and a full-blown, life-altering crisis. Let’s walk through a couple of scenarios to see why a small monthly fee can be one of the best investments you make in your personal well-being.
The Reactive Nightmare Without Protection
Meet Alex. One afternoon, the phone rings. It's a debt collector calling about a credit card bill that's seriously past due—for over $5,000. The only problem? Alex never opened that card.
That single phone call is the first domino to fall. Panic sets in as Alex realizes a thief has been using their identity for months. The real nightmare is just beginning.
The next few weeks become a blur of frustrating phone calls and endless hold music. Alex has to navigate the bureaucratic mazes of the credit card company, the credit bureaus, and the local police department just to file a report. In every single conversation, Alex has to explain the whole story from scratch, dig up documents, and prove their innocence.
The damage keeps spreading. The fraudulent account has tanked Alex's credit score, which gets them denied for a car loan they desperately needed. The stress is overwhelming, causing sleepless nights and affecting their performance at work. It feels like drowning in paperwork with no end in sight.
This is the reality for countless victims. Alex is facing a mountain of work, an emotional drain, and a long, uncertain road to recovery—all because the theft went unnoticed until the damage was already done.
The Proactive Response With Protection
Now, let’s see how this could have gone differently. Meet Taylor, who has an identity theft protection service. One morning, Taylor's phone buzzes with an alert: a hard inquiry just appeared on their Experian credit file from a bank they've never heard of.
Instead of panicking, Taylor opens the service's app. The app confirms the inquiry and asks if it was authorized. Taylor taps "No." Right away, the service gives them a direct phone number and a case reference to contact the bank's fraud department. At the same time, it suggests placing a fraud alert on all three credit files, which Taylor does with just a few more clicks.